Building The Encrypted ICO With Zama
As ICOs return with renewed momentum, their underlying infrastructure becomes critical. Powered by its own FHE stack, Zama introduces a new Sealed-Bid Dutch Auction that enables confidential participation in public ICOs. In this report, we examine the mechanics of Zama’s Public Auction and its future implications for onchain capital formation.
The ICO Renaissance
In 2013, J.R. Willet set out to solve a very specific problem: raise money on the internet instead of going to VCs in Silicon Valley. To do so, he tried something no one had previously attempted: he published a whitepaper for the project he was building, and convinced friends and strangers online to send him Bitcoin in exchange for receiving a newly issued digital token in return. Within a month, Willet had managed to raise over $750,000, and 60 million tokens were then distributed to investors in a public sale.
Willet’s experiment was called Mastercoin, and the OMNI token sale quietly became the first-ever Initial Coin Offering (ICO). Though online crowdfunding had already existed through websites like Kickstarter and Indiegogo, Mastercoin’s ICO marked the first time a project raised capital by selling a freely tradable digital asset on a public blockchain.
A year later, Ethereum blew Mastercoin’s ICO out of the water, raising 31,000 BTC (worth ~$18.6M at the time) of its own. Shortly after, the ERC-20 standard was introduced: a simple framework that made creating and issuing digital tokens trivial. What followed was nothing short of a Cambrian explosion of ICOs. OMNI was the first, but in hindsight it was obviously never going to be the last.
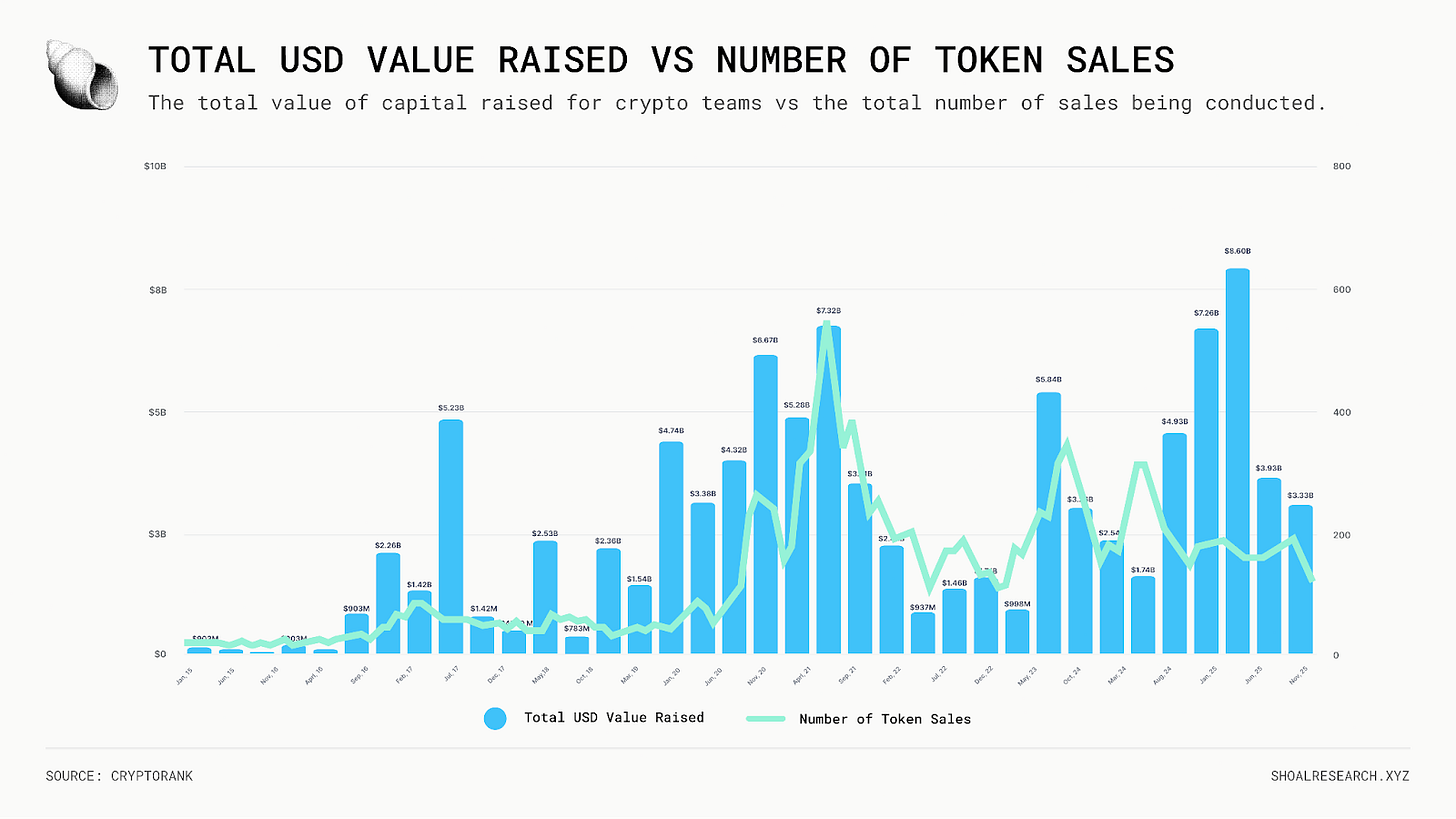
After a few quiet years, demand for ICOs is coming back in force. In 2025 alone, Pump Fun raised $600M for PUMP in the third-largest ICO ever, and teams like Plasma ($50M), Monad ($269M), and MegaETH ($49M) all completed ICOs, with more sales expected in the coming months. Nearly every major sale in 2025 saw strong investor appetite, oversubscribing and selling out in minutes.
Despite fewer token sales since 2021, the total amount of capital raised has continued to grow, concentrating into fewer, higher-quality projects.
Yet this resurgence surfaces something that today’s ICO infrastructure has not yet been able to solve for: confidential investor participation.
Privacy (Or The Lack Thereof) In ICOs Today
Structurally, an ICO isn’t so different from an IPO: it involves a public sale, a launch event, and a freely traded asset. The fundamental difference is in their underlying rails. ICOs run on public blockchains and settle via smart contracts. Investors send funds to a smart contract, which then allocates them digital tokens programmatically based on predefined terms.
This architecture introduces a high degree of public transparency: anyone can independently verify that the sale executed as intended, that token allocations matched contract rules, and that every contribution and refund was accounted for. But this transparency comes with a greater underlying cost: every contribution, wallet, bid, and allocation is permanently visible onchain.
By design, blockchains offer pseudonymity: users interact through randomly generated wallet addresses which are not directly tied to legal identities. However, once a wallet address is linked to a real individual — whether through an exchange withdrawal, an ENS name, or other onchain activity patterns — their entire sale behavior, spanning from contribution size, wallet balance, bidding and sale patterns, and the rest of their transaction history becomes exposed.
Alongside visibility into sale behavior, public blockchains also expose ICO participants to Maximal Extractable Value (MEV) dynamics: value that sophisticated onchain actors (i.e. block builders, validators, and specialized searchers) can capture by reordering, including, or excluding transactions in a block. Simply put, those with visibility into pending transactions can position their own transactions to capture value by front-running, back-running, or sandwiching other participants’ transactions.
For retail investors, this level of transparency is a privacy leak. A single sale interaction can reveal far more than intended: not just how much they contributed, but how much they hold, when they sell, and how they behave across every other onchain activity tied to that wallet. Over time, these disclosures compound, creating persistent visibility into an individual’s financial position and behavior. In practice, this also increases exposure to MEV, as retail users are the least equipped to protect themselves from adverse transaction ordering and value extraction during highly competitive sale events.
For institutions, this level of transparency is simply a non-starter. Participating in a fully public onchain sale broadcasts order flow, position sizing, treasury capacity, and execution behavior to competitors and counterparties. Even the act of bidding can signal strategic intent well before a position is finalized. Combined with MEV dynamics, this creates unacceptable execution risk, where large bids can be detected, priced against, or exploited in real time. As a result, most institutional capital is effectively unable to participate in public ICOs at all, regardless of demand.
Early internet crowdfunding platforms like Kickstarter and Indiegogo did handle personal data, but access to this data was strictly permissioned: backer identities, contribution sizes, and emails were private to the creator and the platform.
By contrast, most attempts to incorporate some form of privacy into token sales have taken form as private, offchain processes, through whitelisted sales, negotiated allocations, data rooms, SPVs, and manual allocation mechanics. These approaches provide confidentiality for their participants, but only by abandoning the very mechanic that made ICOs powerful in the first place: open global access. The result is a bifurcated market in which institutions can only participate through private deals, while retail is pushed into fully transparent public sales that compromise their privacy.
What’s missing is a middle ground: an open, public ICO rail that preserves fairness and transparency at the system level, while providing confidentiality, by default, at the participant level: the allocation logic would remain publicly verifiable, while sensitive participant data would remain private. This type of platform would allow large-scale, rules-based ICOs, supporting tens or hundreds of thousands of participants, without revealing certain details such as individual contribution sizes or linking to prior wallet activity.
Of course, the next question is what this looks like in practice: how would one build public, auditable, yet confidential token sale infrastructure on top of today’s public blockchains?
The Zama Sealed Bid Dutch Auction
Zama is introducing a new Sealed Bid Dutch auction mechanism to bring confidential participation to onchain ICOs. Built on the Zama Protocol itself using FHE, Zama’s launchpad allows investors to participate in ICOs while encrypting sensitive bid and allocation data.
Understanding Zama
At its core, Zama is infrastructure that enables confidentiality for public blockchains using fully homomorphic encryption (FHE). FHE refers to a cryptographic technique that allows computations to be performed directly on encrypted data without first exposing the underlying values. In practical terms, this means data can remain confidential while still being used inside smart contract logic. Inputs are encrypted before reaching the blockchain, and processed in encrypted form through Zama’s confidential execution framework, and can only be decrypted by authorized parties at the end of execution.
Zama implements this capability through the fhEVM, its core confidentiality framework. A small set of specialized smart contracts is deployed on underlying public chains, enabling applications to validate encrypted inputs, manage encrypted state, and coordinate decryption through Zama’s key management system. These contracts can be integrated into existing wallets and frontends, which users can then easily access. Meanwhile, developers can write confidential smart contracts onchain using Zama’s fhEVM Solidity Library and standard EVM tooling.
As a result, sensitive data remains encrypted throughout its entire lifecycle: from the moment it leaves the user, through onchain computation, until the final result is decrypted by an authorized party. This breakthrough unlocks new classes of onchain applications, one of which is the confidential ICO.
How The Sealed Bid Dutch Auction Works
As with a ‘traditional’ ICO, investors deposit assets and place bids on the token to be sold, and once the auction is complete tokens are programmatically distributed to investors. The critical distinction is that, in Zama’s design, bid data is encrypted by FHE and therefore remains confidential throughout the auction process: whereas the bid price is public, the deposit amount and token allocation are not.
Zama uses a Dutch auction format, meaning the lowest bid price is selected as the clearing price as bids are processed in price-descending order until the available supply is exhausted. During bidding, which lasts a total of 4 days, investors can submit encrypted bids. Once bidding ends, the auction contract calculates the clearing piece by selecting the lowest price at which a bid was filled, and distributes tokens to investors accordingly. Investors can then claim their tokens, or a refund if necessary.
Consider an auction with a total supply of 100 tokens to be distributed:
Bob bids 40 tokens at a price of $2. His bid is filled, and now there are 60 tokens left to distribute.
Alice bids 60 tokens at a price of $1. Her bid is filled, and now there are 0 tokens left to distribute.
Mert bids 20 tokens at a price $0.50, but since there are 0 tokens left his bid is not filled.
In this case, the clearing price is thus $1, given that it was the lowest price at which all the tokens were distributed (Alice’s bid). Therefore Bob receives 40 tokens and a $40 refund, Alice receives 60 tokens and no refund, while Mert receives zero tokens and a $10 refund. All tokens sold from the auction are fully unlocked and freely tradable upon claim.
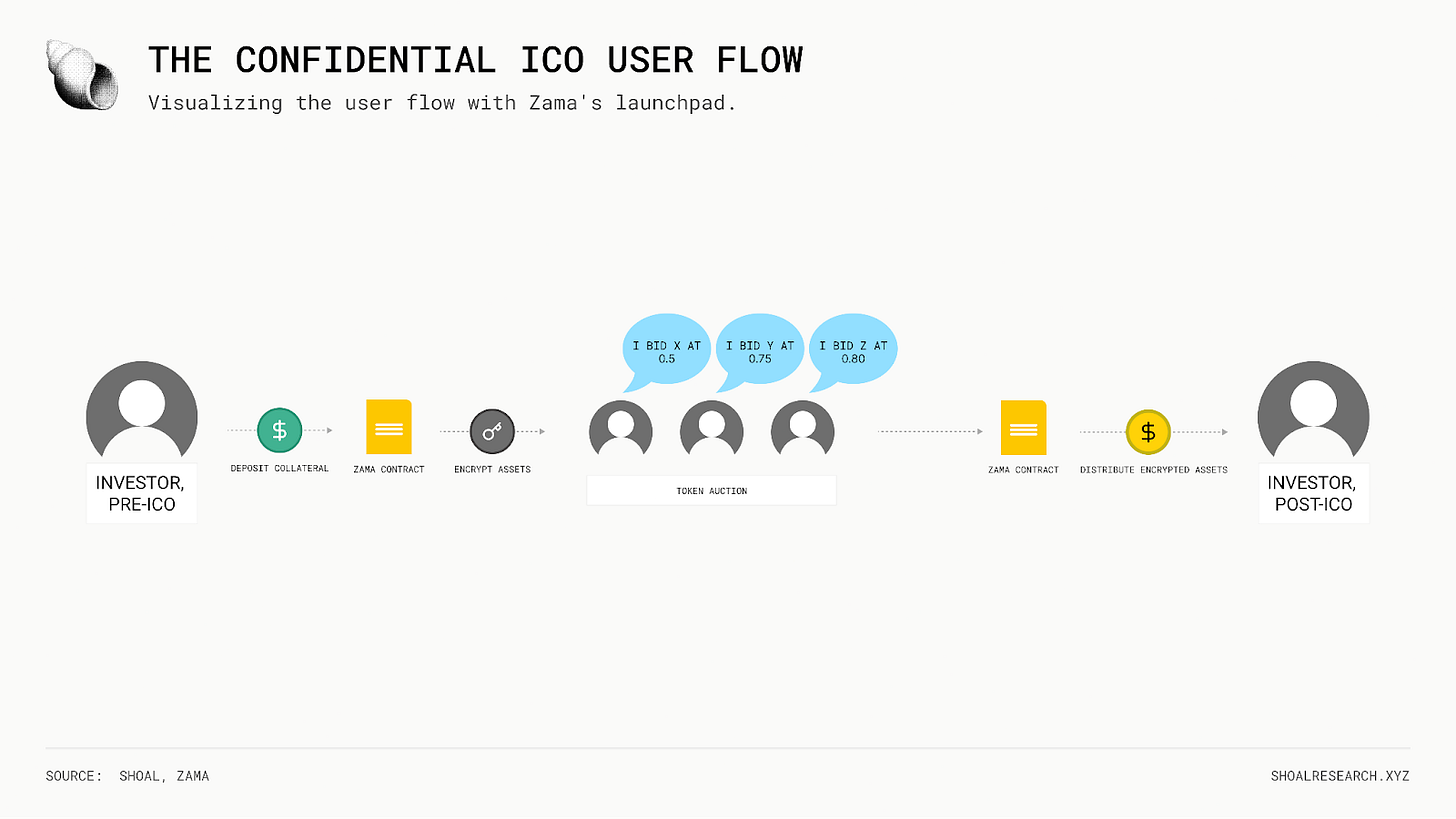
User Flow
By design, the user flow is relatively simple and straightforward.
Investors first encrypt (or shield) the assets they intend to use for bidding. In exchange, they receive confidential “cTokens” at a 1:1 ratio, representing encrypted versions of the underlying collateral. Investors then submit bids for the token being launched at their chosen price, using these cTokens. Throughout the auction, bids can be monitored and managed directly through Zama’s auction interface, without revealing sensitive bid details onchain.
Once the auction concludes, the contract computes final allocations and clearing price. Investors can then claim their outcomes: successful bidders receive their allocated tokens, while any excess collateral is refunded. At this point, investors may either decrypt their remaining cTokens back into standard tokens or continue using them across other confidential applications within Zama’s broader ecosystem.
Technical Mechanics
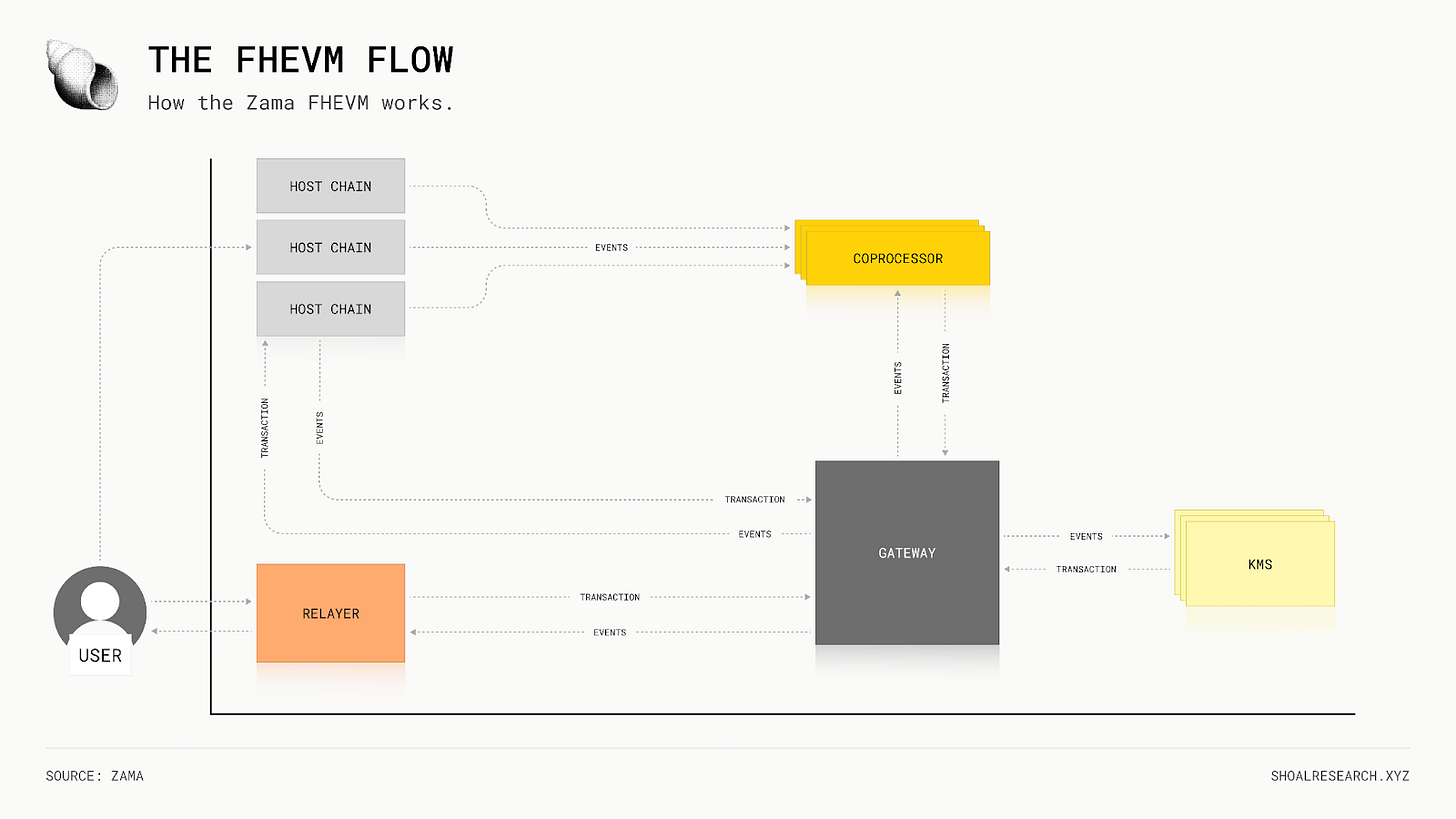
At the core of Zama’s protocol is an FHE system. Rather than exposing inputs, balances, or intermediate values to the blockchain, all sensitive data is maintained in encrypted form throughout contract execution. This encrypted state is preserved under a unified FHE key, allowing smart contracts to operate directly on ciphertext without ever decrypting underlying values during execution.
To break this down further, the execution flow follows a well-defined pattern. A user encrypts an input (x) locally, producing an encrypted value E(x). This encrypted input is submitted onchain, where it cannot be decrypted by validators, block builders, or other applications. Smart contracts then compute directly over encrypted inputs, producing an encrypted output E(f(x)). Only authorized parties can decrypt the final result, while all intermediate computation remains opaque to the blockchain itself.
This execution model is implemented through the fhEVM, Zama’s confidentiality execution framework. The fhEVM operates as a specialized layer on top of existing public blockchains, coordinating encrypted computation, maintaining encrypted contract state, and managing controlled decryption through Zama’s key management system. A small set of smart contracts deployed on the underlying chain handle encrypted input validation, encrypted state transitions, and interactions with the key infrastructure, while remaining fully compatible with existing EVM environments.
When applied to the Auction, these mechanics ensure that the auction state is never represented in plaintext. Assets deposited by participants are immediately converted into encrypted state and represented as confidential balances within the auction contract. Bid evaluation, allocation logic, and refund calculations are all performed over encrypted values, preventing observers from inferring contribution sizes, wallet balances, or allocation outcomes during the auction process.
To implement this in practice, Zama introduces confidential “cTokens”, which serve as FHE-encrypted representations of standard ERC-20 assets. These tokens are issued programmatically when assets are encrypted and are redeemed when assets are decrypted, without exposing balances or transaction history onchain. cTokens are implemented using the ERC-7984 confidential token standard, allowing encrypted assets to remain composable across other confidential applications built on Zama’s protocol.
As a result, sensitive data remains encrypted for its entire lifecycle; from the moment it leaves the user, through onchain computation, until the final result is decrypted by an authorized party. In the context of ICOs, this architecture allows auctions to remain publicly verifiable at the system level, while ensuring that participant-level data remains confidential by default.
The North Star: Growing TVS
Zama’s adoption and growth is framed around a new type of metric: the Total Value Shielded (TVS).
TVS refers to the total amount of economic value that is actively encrypted and kept confidential using Zama’s protocol. Just as total value locked (TVL) became a dominant metric for tracking DeFi liquidity, TVS is meant to serve as a proxy for how much meaningful economic activity is taking place under cryptographic confidentiality.
The intuition is simple. The higher the TVS, the more confidentiality is being exercised across assets, applications, and users. As TVS grows, confidentiality evolves from a niche feature to a systemic property of onchain markets: assets become harder to surveil, applications harder to exploit, and users regain more control over the privacy of their onchain activity.
Zama’s strategy for growing TVS is infrastructure-first. Rather than building and owning end-user applications, Zama is positioned as a chain-agnostic confidentiality layer that other developers, protocols, and platforms can build on top of. Zama provides the primitives for encrypted computation and confidential state, while leaving application design, UX, and go-to-market decisions to application developers.
This way, Zama does not need to directly control demand to drive growth. TVS increases as confidentiality becomes a default property across an expanding set of applications and chains. Adoption is reflected in how broadly encrypted computation is integrated and how much economic value is processed under confidentiality, rather than in usage of any single application.
From a deployment perspective, Zama is designed to be chain-agnostic. The protocol is launching first on Ethereum, with plans to expand across EVM-compatible chains and, longer-term, into non-EVM environments such as SVM-based chains. This multi-chain approach ensures that confidentiality is not siloed to a single execution environment, but can follow users and assets wherever onchain activity migrates to.
TVS in Practice: The ZAMA Token Launch
The first live demonstration of an encrypted ICO will be the Zama’s Sealed-Bid Auction will be Zama’s own token sale. The $ZAMA token launch will be conducted on Ethereum, using the Zama Protocol itself to encrypt bids through FHE.
Zama will sell 8% of the $ZAMA supply through this auction. Participants submit bids onchain while sensitive bid data, including contribution size and allocation, remains encrypted throughout the process. Once bidding concludes, the auction clears transparently according to publicly verifiable rules, and tokens are distributed immediately with no vesting or lockups. In doing so, the Auction intends to bring fair price discovery, global access, and confidentiality to ICOs within a single platform.
This auction will mark the first instance of Total Value Shielded (TVS) flowing through Zama’s protocol in production. Capital contributed to the auction is encrypted end-to-end, allocations are computed over encrypted state, and only final outcomes are revealed, thus serving as a real-world stress test for confidential onchain capital formation at scale.
Use Cases and Applications
While confidential ICOs provide a clear and immediate application, the underlying primitives enabled by Zama’s launchpad can, in theory, extend far beyond token sales. At a high level, any onchain mechanism that relies on bidding, allocation, or competition over scarce resources can benefit from encrypted execution:
NFT Auctions: Encrypted bidding enables sealed-bid NFT sales where bid amounts remain confidential until settlement. This could help prevent bid anchoring, strategic signaling, and enable fairer price discovery.
Prediction Markets: Encrypted bidding introduces a new design space for prediction markets, where individual positions and strategies can remain private during market formation, while outcomes and settlement remain publicly verifiable.
Governance: Encrypted bidding can be applied to onchain governance systems where outcomes are influenced by market signals or competitive inputs rather than simple token-weighted voting. By keeping bids or commitments confidential during the decision process, protocols can reduce signaling effects, cartel formation, and strategic coordination that often distort outcomes in fully transparent governance systems. This can be especially useful in futarchy-style governance, where participants express beliefs through markets tied to policy outcomes. In these settings, encrypted bids help preserve genuine price discovery by preventing participants from anchoring or reacting to visible positions before markets resolve.
Solver Order Flow (PFOF) Bidding: Encrypted bidding can be applied to MEV and order-flow markets, where solvers compete for the right to execute transactions or bundles. This can potentially reduce information leakage around solver strategies, limit copy-trading and reactive bidding, and mitigate winner-take-all dynamics driven via information asymmetries, thus encouraging a more competitive and efficient market for onchain order flow.
Confidential Block Production or Rewards Auctions: In Proof-of-Stake systems, encrypted bidding could be used to allocate block production rights or reward opportunities over defined time windows. Validators would submit encrypted bids for future slots or epochs, with allocations determined programmatically once the auction clears. By keeping bids private, such mechanisms reduce signaling and strategic front-running among validators, while enabling more market-driven allocation of block production rights.
Taken together, these examples show that encrypted ICOs are just one instance of a broader pattern. Any onchain mechanism that relies on bidding, allocation, or competition over scarce resources can potentially integrate and benefit from encrypted execution.
Closing Thoughts
At Shoal, we believe ICOs are positioned for renewed demand if the underlying infrastructure evolves to support confidential participation. Retail investors can participate in public sales without broadcasting their balances, positions, or trading behavior onchain. Institutions can participate without exposing order flow, signaling strategic intent, or introducing execution risk that distorts broader market activity. Both benefit from reduced MEV exposure during highly competitive bidding processes.
Zama introduces a concrete path toward this future by treating confidentiality as first-class infrastructure and orienting the protocol around a clear objective: growing the TVS across the broader onchain economy.
With this in mind, we look forward to a new chapter of confidential onchain capital formation.
Sources
Cryptorank ICO Analytics, cryptorank.io/ico-analytics/
ICO Drops, icodrops.com/
Cryptoasset Market Coverage Initiation: Network Creation. Bloomberg Research, research.bloomberg.com/pub/res/d28giW28tf6G7T_Wr77aU0gDgFQ
“Digital Tulips? Returns to Investors in Initial Coin Offerings.” ScienceDirect, sciencedirect.com/science/article/abs/pii/S0929119920302303
Coin Perspective: J.R. Willett. Medium, medium.com/coin-story/coin-perspective-3-j-r-willet-136ed51a852c
Zama Documentation. Zama, docs.zama.org/homepage/
Zama Protocol Litepaper. Zama, docs.zama.org/protocol/zama-protocol-litepaper
Zama FHEVM Whitepaper. Zama GitHub, github.com/zama-ai/fhevm/blob/main/fhevm-whitepaper.pdf
Zama Public Auction: auction.zama.org
Not financial or tax advice. The purpose of this post is purely educational and should not be considered as investment advice, legal advice, a request to buy or sell any assets, or a suggestion to make any financial decisions. It is not a substitute for tax advice. Please consult with your accountant and conduct your own research.
Disclosures. All posts are the author’s own, not the views of their employer. This post has been created in collaboration with the Zama team. At Shoal Research, we aim to ensure all content is objective and independent. Our internal review processes uphold the highest standards of integrity, and all potential conflicts of interest are disclosed and rigorously managed to maintain the credibility and impartiality of our research.