zkPass: Enabling Verifiable Data Composability
zkPass is redefining privacy & data verification by integrating ZKPs, Multi-Party Computation (MPC), and 3P-TLS. It enables verifiable, privacy-preserving data sharing across finance, healthcare, etc.
Exploring the History of Privacy and Data Verification
The history of privacy and data verification has evolved through a series of methods and technologies that reflect the changing needs of societies, businesses, and individuals. Before the advent of modern cryptographic protocols like zkTLS (zero-knowledge transport layer security), privacy and data verification were primarily handled through more traditional means, relying on trust, physical verification, and centralized systems.
In ancient times, privacy was maintained largely through physical barriers or social norms. For instance, in medieval times, royal seals were used to authenticate documents and ensure privacy. These seals act as verifiable proof that the document came from a trusted source, although they were still vulnerable to forgeries. Similarly, handwritten letters with private information required trusted messengers to carry them safely, often leading to incidents of espionage or breach of trust, as there was no secure way to ensure the integrity of the transmitted data.
As societies evolved, the need for more formalized data verification grew. In the 19th century, the advent of the postal system saw the rise of envelopes and letters of authentication. People relied on trusted institutions like banks and notaries to verify the authenticity of documents, as these entities were trusted to validate identities and certify information. For example, the birth certificate, a vital document for personal identification, could be verified by a government official or an appointed institution. This was a significant leap from manual methods, but it still required individuals to trust centralized authorities. Similarly, checks and paper-based business contracts, verified by signatures, still dominate.
However, these methods had their limitations, especially regarding privacy, as sensitive information could be accessed by unauthorized parties or manipulated without sufficient safeguards.Data privacy and verification took on a more technical role in the digital age. The invention of public-key cryptography in the 1970s, with the development of algorithms such as RSA, allowed for secure communication over digital channels, revolutionizing how privacy was maintained. Encryption has become a cornerstone of privacy in the digital world, with users relying on methods like SSL (Secure Sockets Layer) certificates to secure their data when browsing websites. However, while SSL provided a level of encryption, it was not foolproof and still had the potential for man-in-the-middle attacks where a third party could intercept data and alter it. In e-commerce, for example, when people made online transactions, they relied on SSL certificates issued by trusted authorities to secure sensitive payment information, yet security breaches like the infamous Heartbleed vulnerability demonstrated that even encrypted connections could be susceptible to flaws.
Fast forward to the early 2000s, and blockchain technology emerged as a potential solution for both data privacy and verification, with its decentralized nature promising to eliminate the need for centralized authorities to verify transactions. Bitcoin, introduced in 2009, offered a way to verify the integrity of financial transactions through a distributed ledger, allowing users to engage in financial exchanges without revealing sensitive information, as all transactions were encrypted and recorded publicly but pseudonymously. This was a significant advancement in terms of privacy, as individuals could maintain control over their data, but it was not without its limitations, such as scalability and transaction costs.
The introduction of Zero-Knowledge Proofs (ZKPs) marked a new frontier in privacy and data verification. ZKPs allow one party to prove to another party that a statement is true without revealing any other information about the statement itself. This cryptographic method has gained significant traction in recent years, especially with the rise of privacy-focused cryptocurrencies like Zcash, where users could prove they owned a particular amount of cryptocurrency without revealing their balance or transaction history. zkTLS, a cryptographic protocol combining ZKPs with Transport Layer Security (TLS), represents the next step in ensuring secure communication over the internet, allowing for encrypted, private exchanges where the authenticity of the message can be verified without revealing the content itself.
Imagine a future scenario where zkTLS is used in everyday life. A person enters a café and orders coffee. Instead of showing a physical ID card or revealing sensitive details, the person can use their phone to provide a zero-knowledge proof of age, which would validate that they are over the legal drinking age without disclosing their actual birth date. Similarly, in a corporate setting, an employee could prove their qualifications for a particular project using zkProofs without sharing the actual contents of their resume or personal data, safeguarding their privacy while still enabling the verification of their credentials.
The stories of privacy and data verification are constantly evolving. In earlier times, trust was built on physical barriers, human intermediaries, and written agreements. As technology advanced, digital encryption became the cornerstone of data security, but it often still required a level of trust in centralized authorities or entities. Blockchain, with its decentralized approach, broke new ground, but privacy and scalability challenges remained.
Now, ZKPs and skills are paving the way for a future where privacy and verification coexist seamlessly, offering individuals complete control over their data without compromising on trust or security. The shift is driven by declining costs, improved performance, and increased practical applications like Aligned Layer, Risk Zero, Succinct Labs, etc. ZK proofs are now cheaper than traditional consensus-based verification, making them a compelling alternative for blockchain scalability and data security. Additionally, advancements in binary fields and hardware acceleration are optimizing ZK computations, reducing inefficiencies that previously slowed adoption.
Industries beyond crypto are recognizing the potential of ZKPs in secure identity verification, financial transactions, and compliance. From proving financial integrity without exposing transaction details to verifying credentials without revealing personal data, ZKPs are reshaping digital trust. As adoption expands, we are approaching a future where ZKPs become the standard for secure, efficient, and private verification across various sectors, including finance, enterprise security, and Web3 applications.
Overview
zkPass is a private Oracle protocol that enables private internet data to be verifiable on-chain. Built on top of zkTLS, which is composed of 3P-TLS and hybrid ZK technologies, zkPass provides tools and applications for secure, verifiable data sharing with privacy and integrity assurances from any HTTPS website without requiring OAuth APIs. It is designed to serve as a private data oracle, leveraging Vector Oblivious Linear Evaluation (VOLE) to create efficient commitments, commonly referred to as VOLE-Based Zero-Knowledge Proofs (VOLE-ZK).
zkPass allows users to selectively prove various types of data, such as legal identity, financial records, healthcare information, social interactions, and certifications. These zero-knowledge proof computations are performed locally and securely, ensuring that sensitive personal data is not leaked or uploaded to third parties. They can be used for AI, DePIN, DID, lending, and other financial and non-financial applications.
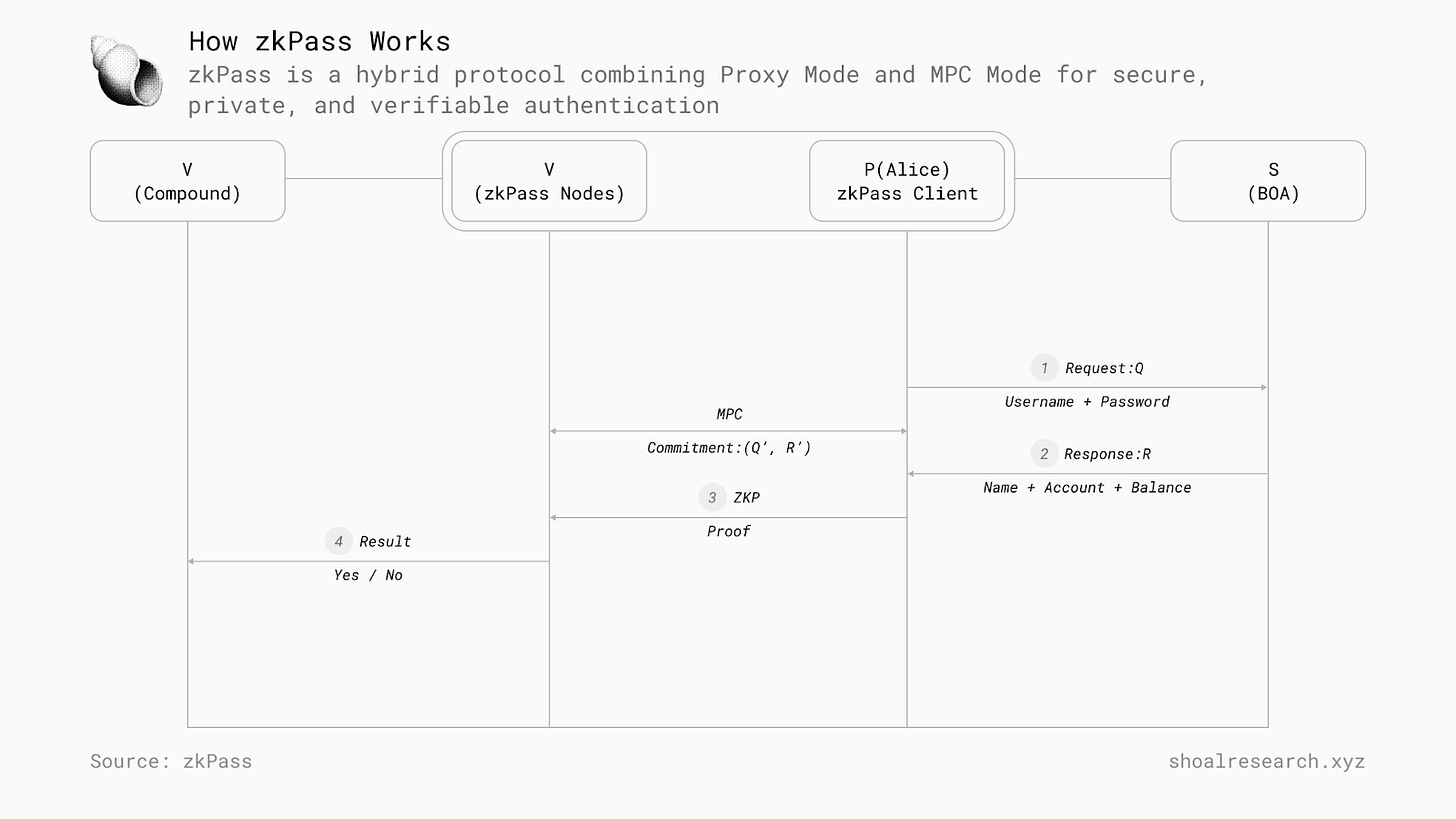
Wherever there is a need for trust and privacy, zkPass can be a solution. zkPass proposes a new paradigm for the traditional data validation and confirmation process, where the verifier is positioned between the prover and the data source. The prover uses the verifier as a proxy, utilizing its access token to retrieve data from the data source. Subsequently, by using the VOLEitH technique, a publicly verifiable proof is generated locally and sent on-chain. This process ensures the verifier remains unaware of the prover's personal information.
Why zkPass?
zkPass, a private data protocol, is seen as the best protocol in its niche due to various reasons, including privacy-preserving of data, anti-cheating mechanism, verifiability of data, seamless integrations with other applications, and zkPass memory efficiency.
Privacy-preserving of data
zkPass works by allowing users to create a digital identity that can be verified without exposing the actual information. For example, a user could prove they are over a certain age without disclosing their full birthdate, or they could authenticate their school degree to access services without revealing the exact university or other personal details. This functionality is achieved through ZKPs, which ensure that only the necessary data is shared and that it cannot be reverse-engineered to expose sensitive information. This method allows zkPass to address key concerns around online privacy, enabling individuals to participate in digital services confidently without sacrificing their security.
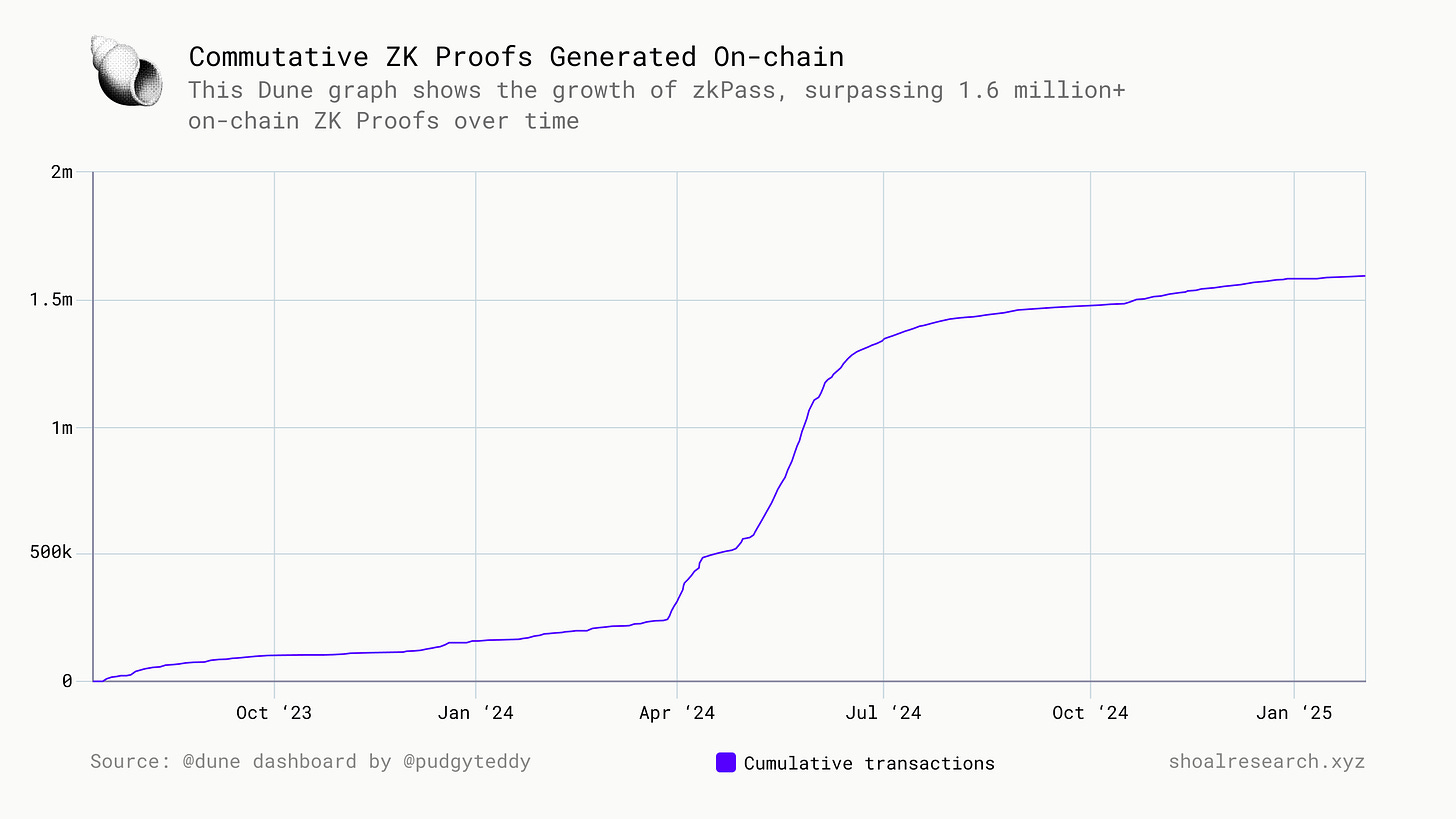
The adoption of zkPass has seen impressive growth, with over 4.5 million cumulative ZKPs generated over time and 1.6 million+ onchain ZK Proofs generated to date. Additionally, the platform has facilitated 500K+ unique wallet addresses, demonstrating strong user engagement and adoption. (Source: Dune Dashboard)
Verifiability of data
In traditional TLS, two parties (client and server) exchange encrypted data to secure communications. However, zkPass introduces a third party into the TLS handshake, which serves to independently validate the authenticity and origin of the data being exchanged. This three-party approach enhances the security of data provenance because the third party can verify the integrity of the communication without actually accessing the private data itself. This enables both verifiability and privacy in transactions, offering a higher level of security for sensitive information like digital identities or credentials.
In the context of zkPass, users can authenticate themselves, prove attributes (e.g., age, location), or conduct transactions without exposing private information by using the decentralized MPC nodes that can verify a user's data integrity before generating a ZKP. It ensures that only the relevant proofs of data are shared, while the actual underlying private data is never disclosed. This approach offers robust privacy protection while guaranteeing the integrity and authenticity of data across digital platforms.
Integrations with other Applications
zkPass seamlessly integrates with any HTTPS-enabled website, ensuring privacy and security without the need for complex APIs or licenses. By leveraging Zero-Knowledge Proofs (ZKPs) and a redesigned three-party TLS protocol, zkPass allows users to authenticate and prove specific attributes without revealing sensitive data. This ensures compatibility across a wide range of applications, offering a smooth, privacy-first user experience while maintaining robust security and data provenance.
zkPass has been gaining traction with the rise of Zero-Knowledge (ZK) use cases, integrating 57 partners and 74+ data sources for privacy-preserving data verification. It is collaborating with leading projects to enable real-world applications, including:
Plume Network – Facilitating verifiable web-private data for secure real-world asset ownership and tokenization on RWAfi.
Push Chain – Enhancing dApp interactions with ZK Proofs and Universal Shared State, ensuring user data privacy.
These partnerships reinforce zkPass's role in simplifying secure digital identity verification across diverse sectors.
Memory-Efficiency
To achieve millisecond-level Zero-Knowledge Proof (ZKP) generation locally in a browser environment, zkPass utilizes a VOLE-based Interactive Zero-Knowledge Proof (IZK) approach, offering efficient memory usage and rapid computation. VOLE (Verifiable Oblivious Linear Evaluation) reduces the computational and memory overhead by eliminating the need for storing large intermediate values, making it ideal for resource-constrained environments like browsers. This allows for the parallelization of computations using Web Workers, optimizing performance while maintaining low latency.
Anti-Cheating Mechanisms
The anti-cheating mechanism in zkPass is designed to ensure the integrity and authenticity of data exchanged between clients and servers, safeguarding against tampering or fraudulent activities. It uses zero-knowledge proofs to validate both the requests sent by clients and the responses received from servers. The mechanism verifies that the client's request data is correct by checking encrypted request data against expected values while also ensuring that the URL provided by the client matches a predefined template. On the response side, zkPass verifies that the encrypted response matches the expected ciphertext, ensuring the integrity of the data received. Additionally, it checks that response attributes align with a specified template and validates the correctness of the values returned. By employing these checks, zkPass prevents malicious actors from exploiting vulnerabilities to manipulate data, thus enhancing the overall reliability and credibility of the system and ensuring trust in the data exchange process.
How does zkPass work?
The zkPass protocol was designed and implemented in two modes: proxy mode and MPC mode. In the proxy mode, the prover(P) communicates with the server(S) through the verifier(V) as a proxy, while in the MPC mode, both the prover(P) and verifier(V) act as a client to communicate with the server(S). These two modes collectively form Hybrid Mode, providing zkPass with the flexibility to operate efficiently across various scenarios. Typically, the zkPass protocol operates efficiently in Proxy Mode. However, a small number of TLS servers do not support this mode, meaning they block the same account’s requests originating from different IP addresses. In such cases, the protocol switches to operate in MPC mode.
Proxy Mode
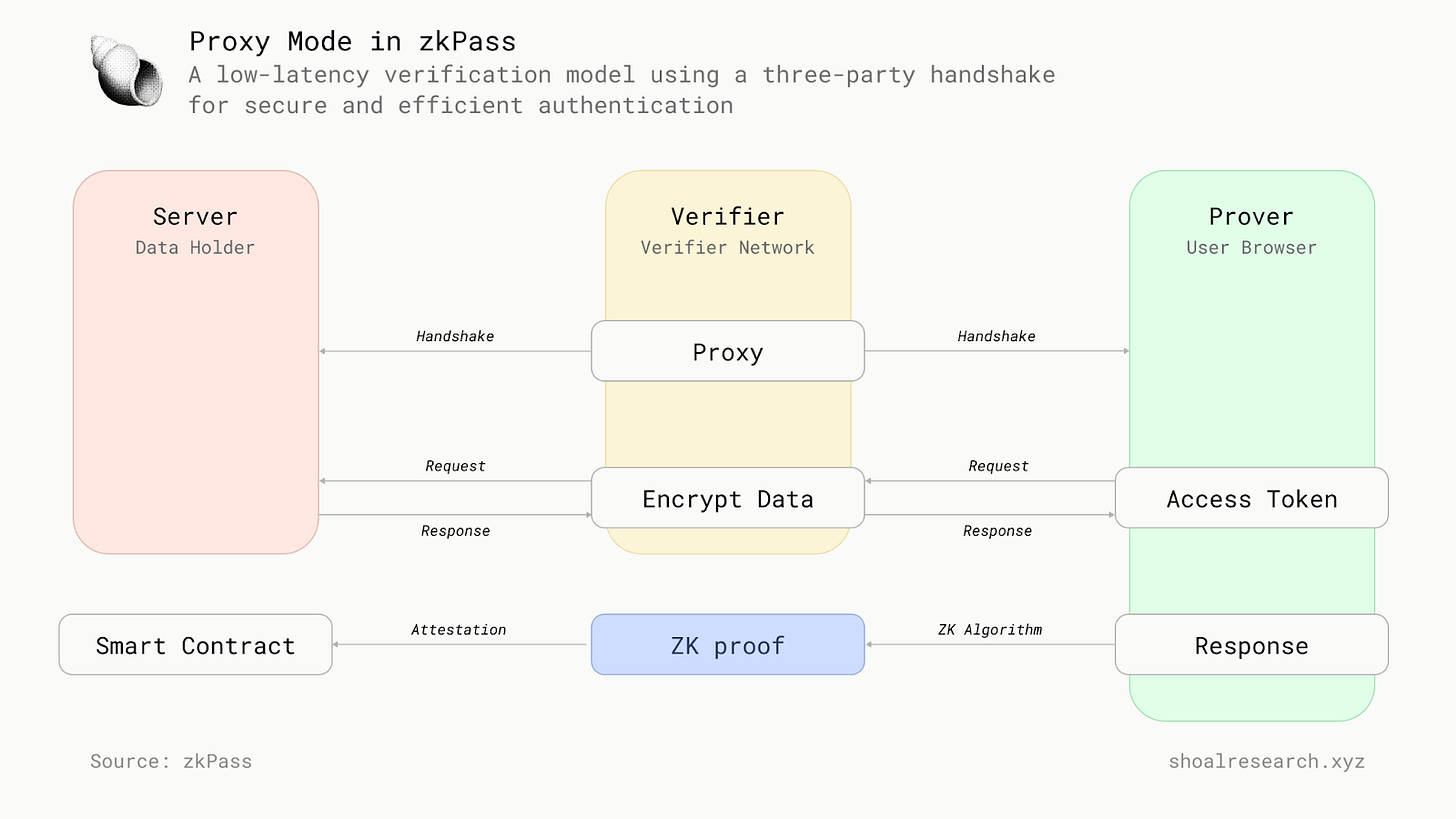
In Proxy Mode, we propose having V act as a proxy between P and S. In this setup, P communicates with S through V, which allows V to record the traffic for later verification. The modified protocol flow is designed to maintain security while improving efficiency. The proxy model has lower latency when compared to the MPC model, making it better suited for large-scale, real-time client applications.
The protocol begins with a three-party handshake involving P (prover), V (verifier), and S (server), where cryptographic parameters are established, ensuring mutual authentication between the parties. Following the handshake, P commits to her key share (Kp), preventing any later alterations to her key share and ensuring she cannot manipulate the session to generate fraudulent proofs. This commitment occurs before P learns the complete session key (K). Subsequently, V reveals his key share (Kv) to P, who, combining both key shares, computes the full session key (K = Kp + Kv). With the session key, P continues the TLS session with S, while V acts as a proxy, recording all the traffic between P and S. After the session concludes, P generates proof about the recorded session, which is then verified by V.
To confirm the server's identity during the three-party handshake, V checks the server's signature on a fresh nonce, as per standard TLS procedures. The integrity and privacy of the verifier are preserved because, assuming TLS is secure, a malicious V cannot undermine the integrity or privacy of the TLS session between P and S. However, ensuring the integrity of the prover requires certain network conditions. V must have a stable connection to S throughout the session and prevent P from interfering with the messages exchanged between V and S, such as through BGP hijacking. Since attacks like BGP hijacking are difficult to execute and are largely mitigated by ICP and CSP, these network requirements are generally acceptable and can be considered negligible in practical scenarios.
The Proxy Mode in the zkPass protocol enhances efficiency and performance by simplifying the communication flow and eliminating the need for intensive cryptographic computations after the handshake phase. Since no complex cryptographic operations are required during the rest of the session, the protocol becomes faster and more efficient due to the reduced cryptographic workload. While this approach is more universal, it introduces an additional trust assumption for the proxy and requires not only a ZK solution that’s affordable for the client but also special magic tricks to bypass the data source’s WAF.
VOLEitH Protocol
To design the zkPass protocol, the VOLEitH protocol, which is suitable for authorizing TLS, was used. The VOLEitH protocol was integrated to achieve an interactive argument system, which is then made non-interactive using the Fiat-Shamir transform. The VOLEitH protocol was implemented into zkPass using SoftSpokenOT [ROY22], VOLE-ZK [YSWW21], and Fiat-Shamir transform [FS87].
zkPass utilizes the VOLE-ZKs, which are much more efficient than SNARKS. VOLE-ZKs naturally handle linear computations, enabling fast and low overhead, which makes them more suitable for authorizing TLS data. They avoid the need for a trusted setup and do not require large memory or extensive calculations for proof generation, making them affordable for clients. However, VOLE-ZK proofs are interactive, necessitating the verifier’s continuous online presence and potentially introducing risks of collusion.
The zkPass protocol employs the VOLEitH technique, transforming the VOLE-ZK protocol into a non-interactive form. This ensures swift and efficient proof generation directly in the browser and device, addressing the limitations of both traditional SNARKs and VOLE-ZKs. By doing so, zkPass combines the efficiency of VOLE-ZK proofs with the convenience of non-interactivity, making it a practical and secure solution for authorizing TLS data.
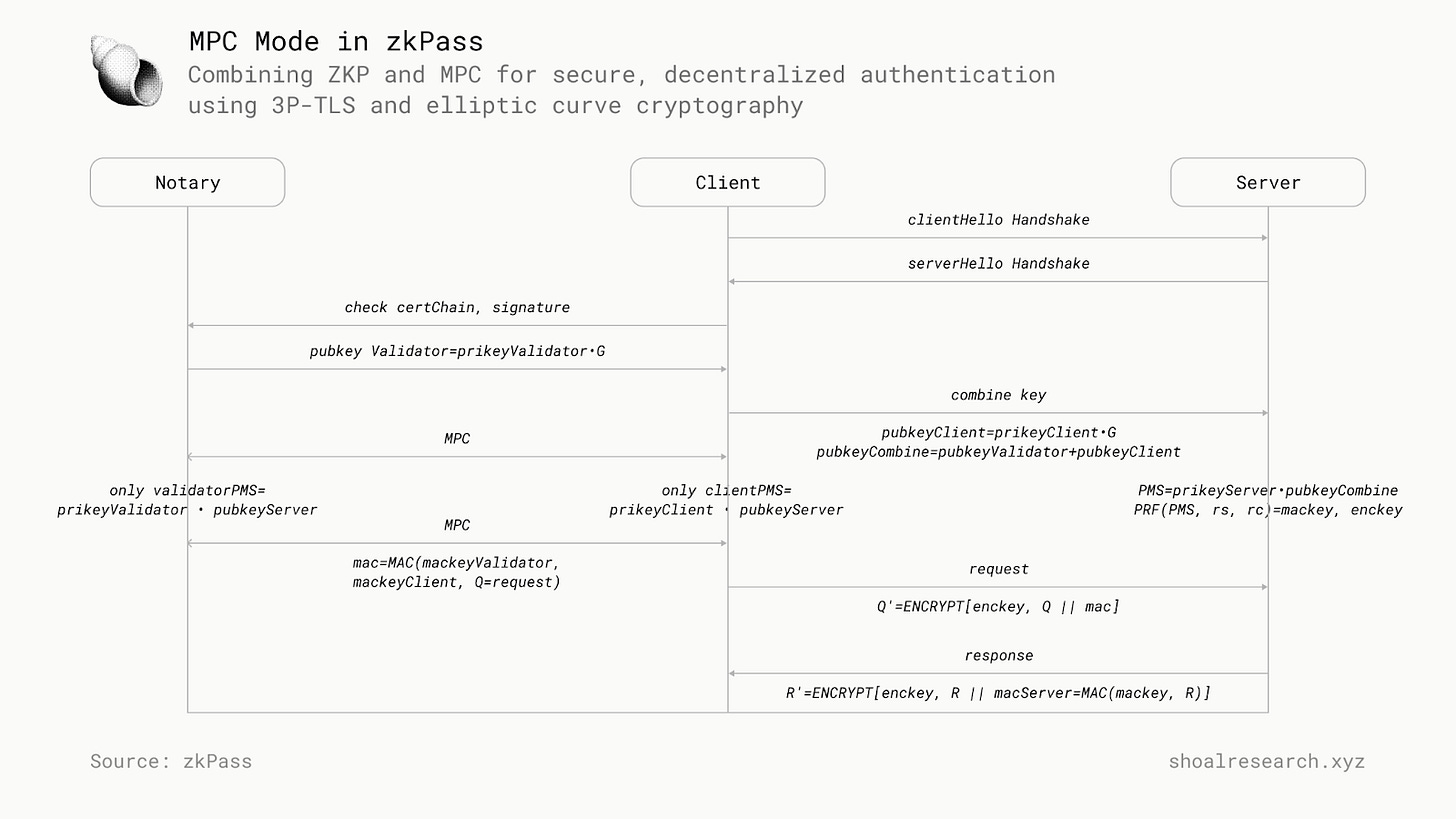
MPC Mode
In MPC Mode, zkPass utilizes a hybrid approach that combines ZKP and MPC technologies to achieve 3P-TLS. Both the P and V work together as a single client to establish secure communication with S. They achieve this through a series of stages based on the elliptic curve Diffie-Hellman (ECDH) protocol, enhanced with MPC and OT techniques.
Three-Party Handshake
The first stage of the protocol is a three-party handshake between P, V, and S, where they work together to generate the pre-master key. P and V each receive a share of this key using Oblivious Linear Evaluation (OLE)-based multiplicative-to-additive (MtA) or additive-to-multiplicative (AtM) schemes, which support additive homomorphism. The pre-master key is divided, with P and V each getting one half, while S retains the full key.
To ensure authenticity and prevent the client from impersonating fake websites, after the client and server exchange greetings, the server provides its certificate. During the key exchange phase, the server also signs the public key with its private key from the certificate. This allows V, within the client, to verify the certificate and signature, confirming the server’s identity and establishing trust in the data source.
The second stage of the protocol is key derivation, where P and V work together using Garbled Circuit (GC) to generate two session keys from the pre-master key: the encryption key (enc_key) for data protection and the message authentication code key (mac_key) for data integrity. Notably, V only holds a share of the mac_key and has no access to the enc_key, ensuring that V cannot view P’s private information. P also holds a share of the mac_key, giving access to identity-related data but without the ability to tamper with it. Any tampering can be detected by verifying the authenticity of messages using the mac_key.
The MPC algorithm in zkPass has been significantly optimized in several areas, including communication time, hash functions for the Garbler and Evaluator, OT operations, and memory copying. These improvements have increased efficiency by more than threefold. A new AES128 proof method has also been introduced, reducing the number of blocks by 300 times and speeding up Garbler/Evaluator execution by tenfold. zkPass uses silent OT, minimizing offline network communication during OT generation. For GC, zkPass implements Three Halves Make a Whole and Stacked GC, which reduces the size of the Garbled Tables, leading to less communication and faster execution. Overall, these optimizations have greatly reduced the runtime of the entire MPC process, making zkPass much more efficient.
In the final stage of the zkPass protocol, the client creates a ZKP for public verification. After the 3P-TLS phase, the prover obtains the complete data and uses the VOLEitH process to generate a proof. Since this step is similar to the process used in proxy mode, we won’t go into the details here.
Hybrid Mode
In hybrid mode, zkPass switches seamlessly between proxy mode and MPC mode, which then allows the protocol to adapt to various network environments and server policies without compromising efficiency or security. Proxy Mode ensures high performance with minimal cryptographic overhead, while MPC Mode takes over when certain servers block requests from multiple IP addresses, maintaining privacy and security. The use of VOLEitH further enhances efficiency by avoiding the heavy computational and memory demands of traditional cryptographic systems like SNARKs. The key features of the zkPass hybrid mode are:
Dynamic Mode Switching: It adapts to varying characteristics of data sources (e.g., network environments and server policies) by dynamically switching between models to ensure maximum compatibility and an optimal client experience.
The hybrid mode combines memory efficiency from interactive zero-knowledge proofs and incorporates the public verifiability of non-interactive zero-knowledge proofs.
Use Cases
zkPass redefines data verification and privacy-preserving in the digital age. With its innovative combination of Multi-Party Computation (MPC), Zero-Knowledge Proofs (ZKP), and 3-party Transport Layer Security (3P-TLS), zkPass empowers individuals to take control of their private data and safeguard their privacy across various aspects of their lives. The use cases of zkPass cut across various industries from decentralized finance, DAO, and NFT to online banking, education, medical, and healthcare.
Legal Identity Check: zkKYC
Traditional KYC solutions face several challenges, including privacy concerns, as they often require individuals to disclose extensive personal information, raising risks of identity theft and unauthorized data access. Additionally, centralized data storage systems are vulnerable to breaches, and businesses incur high costs for implementation, training, and compliance efforts. The process is also slow, involving manual verification and numerous interactions, which can delay onboarding. Inefficiencies arise from fragmented data management, and a lack of interoperability forces customers to repeat the KYC process for different services. Compliance with ever-changing regulations is difficult, and fraud remains a constant risk, despite verification efforts.
zkKYC, based on zkPass, provides a solution by using zero-knowledge proofs and multi-party computation to address these issues. It ensures privacy by allowing users to verify their identities without disclosing sensitive information. By decentralizing data storage, zkKYC reduces the risk of data breaches and gives users more control. The process is cost-effective, faster, and more efficient, reducing manual work and improving data management. zkKYC also offers interoperability, allowing seamless sharing of verified information across services, and adapts to changing regulations, ensuring ongoing compliance. Moreover, its secure methods, including zero-knowledge proofs, reduce fraud risks.
Use cases for zkKYC include tenant screening in rental properties, where landlords can verify identity and financial background without accessing sensitive data. It can be employed for age and identity verification in online gaming platforms, social media, and the gig economy, ensuring compliance and security while protecting privacy. Additionally, zkKYC can be used to validate digital signatures and authenticate users on secure messaging platforms, safeguarding sensitive communications and transactions.
Finance
As digital finance continues to grow, several challenges have emerged, including identity theft and fraud, which result in significant financial losses and reputational damage to both individuals and institutions. Privacy concerns are also rising, as users are increasingly worried about protecting their sensitive personal and financial information when interacting with financial services. Financial institutions also struggle with meeting KYC and AML compliance requirements while minimizing user friction and maintaining privacy. Additionally, there is a need for interoperability between DeFi and CeFi platforms, requiring a secure identity solution that seamlessly integrates across various financial applications.
zkPass, a composable, privacy-preserving identity protocol utilizing zero-knowledge proofs (ZKP) and multi-party computation (MPC), addresses these challenges by offering secure and privacy-preserving solutions. It enables proof of funds, credit scoring, insurance claims, risk assessment, transaction screening, and user access control, all while protecting sensitive user data. zkPass can be integrated into DeFi platforms to enhance trust and reduce fraud. Streamline lending processes by verifying creditworthiness without exposing personal details and secure insurance claim verification. It also ensures privacy for charitable donations, fosters trust in crowdfunding by verifying identities and supports secure, private interactions across various financial services.
Education
The education sector faces a range of challenges, particularly concerning privacy, security, and efficient data sharing. One of the main concerns is protecting minors' privacy, as educational institutions are responsible for handling the sensitive data of minors and must comply with strict privacy regulations. Another challenge is ensuring academic integrity, as preventing cheating and plagiarism is essential for maintaining high educational standards. In research, confidentiality is crucial, as projects often involve sensitive information and intellectual property that must be safeguarded. Furthermore, international data sharing is increasingly necessary for cross-border collaborations, but it requires secure methods that comply with various regional data protection regulations. Additionally, verifying the authenticity of academic credentials, such as degrees and certificates, is vital for maintaining trust and credibility in the education system.
zkPass, a privacy-preserving identity solution, addresses these challenges effectively. It offers secure and verifiable identity verification for educational purposes, ensuring compliance with privacy regulations for minors and protecting sensitive data. zkPass supports the verification of academic degrees and transcripts, streamlining the process of confirming qualifications while minimizing privacy risks. It also enables secure and private interactions during online exams, preventing plagiarism and ensuring academic integrity.
For research, zkPass facilitates secure collaborations while safeguarding intellectual property and sensitive research data. Moreover, it provides a solution for international data sharing, allowing educational institutions to securely share data across borders while adhering to regional data protection regulations. Through blockchain-based credential management, zkPass simplifies the verification of educational credentials, promoting trust in global research collaborations.
By addressing the specific challenges of privacy, security, and data sharing, zkPass has the potential to transform the education and research sectors. It enhances learning experiences, streamlines academic processes, and fosters secure and privacy-preserving research collaborations, all while ensuring compliance with complex data protection regulations. As the sectors continue to embrace digital technologies, zkPass is poised to play a key role in shaping a secure, inclusive, and collaborative future.
Medical & Healthcare
The medical and healthcare sectors face several critical challenges related to privacy, security, and efficient data sharing. Privacy protection is a major concern, as safeguarding sensitive patient information and ensuring compliance with data protection regulations like HIPAA and GDPR are essential. Healthcare organizations also face difficulties in securely sharing medical records and health information between patients, healthcare providers, and other stakeholders. The sector struggles with reducing administrative burdens and minimizing errors associated with manual identity verification and data-sharing processes. Additionally, there are issues related to fraud prevention, particularly in insurance claims and prescription management, where secure identity and data verification are needed. Regulatory compliance is another challenge, as healthcare organizations must meet stringent data protection and privacy obligations. Furthermore, interoperability remains a hurdle, as the sector requires secure and efficient data sharing across different platforms and organizations to enhance collaboration and coordination.
zkPass, a privacy-preserving identity solution, offers several solutions to these challenges. It enables secure patient identity verification, ensuring that personal health data is protected in compliance with data privacy regulations. zkPass can be integrated into blockchain-based electronic health records to facilitate secure, private access to medical records while maintaining data integrity. It supports secure sharing of medical records between healthcare providers and stakeholders, improving data accessibility and reducing administrative overhead. zkPass also plays a crucial role in clinical trial participant verification, ensuring that participants' identities and health data are kept confidential while fostering trust in the research process.
Additionally, zkPass can streamline health insurance claim verification and prescription management, reducing fraud and ensuring the privacy of sensitive health information. For telemedicine and remote consultations, zkPass ensures secure identity verification and the safe sharing of health information. It can also be used in emergency medical services, providing responders with rapid, secure access to critical patient data, such as medical history and allergies, without compromising privacy.
zkPass further supports cross-border health data sharing, allowing healthcare providers in different countries to share patient data securely and privately, enabling seamless care coordination for international patients. By adopting zkPass, healthcare providers can implement patient portals that offer individuals secure access to their health information while maintaining control over their data privacy. In precision medicine, zkPass facilitates the secure sharing of genetic and health data, enabling researchers and healthcare providers to develop personalized treatment plans based on patient's unique needs.
By addressing the challenges related to identity verification and secure data sharing, zkPass has the potential to significantly improve privacy, security, and efficiency in the healthcare sector. It enhances patient experiences, streamlines processes, and ensures compliance with data protection regulations. As the healthcare industry continues to adopt digital technologies, solutions like zkPass will play a pivotal role in creating a more secure, patient-centered, and collaborative future.
Conclusion
In conclusion, zkPass represents a significant breakthrough in the pursuit of privacy and secure data verification in the digital era. As the internet continues to evolve and expand, so does the need for robust methods to protect personal information, especially as individuals increasingly share sensitive data for various online services. With cyber threats becoming more sophisticated and pervasive, the ability to securely verify data without exposing unnecessary personal details is more important than ever. zkPass offers a unique and effective solution by leveraging cutting-edge cryptographic techniques such as zkTLS and VOLE-ZK, allowing users to authenticate and prove credentials while preserving their privacy.
The core innovation of zkPass lies in its ability to utilize zero-knowledge proofs (ZKPs), a method that allows one party to prove to another that a statement is true without revealing the underlying information. This ensures that sensitive personal data—whether it pertains to an individual’s identity, qualifications, financial status, or other sensitive attributes—can remain confidential while still being verifiable. For example, a person can demonstrate their age, financial stability, or educational background without exposing their date of birth, salary details, or the name of the institution they graduated from. This greatly reduces the risks associated with data breaches, as only the required proof is shared, not the full set of sensitive information.
The integration of zkPass into existing infrastructures, particularly through its compatibility with HTTPS websites, is a key feature that sets it apart from other privacy solutions. Traditional privacy-preserving systems often require complex setups, such as new APIs or custom protocols, which can be time-consuming and difficult to implement. However, zkPass is designed to work seamlessly within existing digital ecosystems, allowing users to enhance their privacy without the need for substantial changes to the websites or platforms they use. This ease of adoption makes it an attractive option for organizations and developers seeking to improve data security and privacy without significant overhead or disruption to their existing operations.
Moreover, zkPass's hybrid approach, combining proxy mode and multiparty computation (MPC), further enhances its flexibility and scalability. Proxy mode allows data to be relayed securely between parties while maintaining privacy, while MPC ensures that sensitive computations can be carried out collaboratively among multiple parties without exposing private data. This flexibility makes zkPass adaptable to a wide range of use cases, from simple authentication processes to more complex applications in fields like finance, education, and healthcare. For example, a financial institution could use zkPass to verify an individual's creditworthiness without ever needing to access or store sensitive financial details, reducing the likelihood of data exposure in case of a breach.
The implications of zkPass extend far beyond mere privacy enhancement; it also facilitates a shift toward a more trustworthy, verifiable digital environment. As more aspects of daily life move online, the need for robust and verifiable credentials is increasing. Whether for accessing government services, enrolling in educational programs, or proving one’s employment history, zkPass offers a secure method of verification that can be universally adopted. By providing verifiable proof without compromising privacy, zkPass empowers individuals to maintain control over their data while interacting with digital platforms.
In sectors like healthcare, for instance, zkPass could allow individuals to prove that they are eligible for certain medical treatments or insurance policies without revealing their complete medical history. Similarly, in education, students could prove that they hold specific degrees or certifications without exposing grades or other private academic records. This could revolutionize how credentials are managed and shared, creating a more secure and efficient way for institutions to verify qualifications without needing to store or share unnecessary private data.
As we move toward a future where privacy is a growing concern and data security is paramount, zkPass is poised to play a central role in reshaping how we interact with digital services. It strikes a critical balance between privacy and verifiability, two often conflicting goals in the current landscape of data-sharing technologies. With its seamless integration, cryptographic foundation, and flexibility across multiple sectors, zkPass sets a new standard for privacy-preserving data sharing. It ensures that as digital systems become more interconnected, individuals can still maintain control over their personal information, thus fostering greater trust and security in online interactions. Ultimately, zkPass is a privacy tool and a catalyst for building a more secure, transparent, and privacy-respecting digital ecosystem. As the world increasingly turns to digital solutions, zkPass could become a foundational technology, ensuring privacy remains at the forefront of online engagement.
References
Technical Overview Offical Doc. https://zkpass.gitbook.io/zkpass/overview/technical-overview-v2.0
Introducing the Hybrid Mode of zkTLS: A zkPass Innovation. https://medium.com/zkpass/introducing-the-hybrid-mode-of-zktls-a-zkpass-innovation-9ec18b36f397
zkTLS—The Cornerstone of Verifiable Internet. https://medium.com/zkpass/zktls-the-cornerstone-of-verifiable-internet-da8609a32754
Not financial or tax advice. The purpose of this post is purely educational and should not be considered as investment advice, legal advice, a request to buy or sell any assets, or a suggestion to make any financial decisions. It is not a substitute for tax advice. Please consult with your accountant and conduct your own research.
Disclosures. All posts are the author's own, not the views of their employer. This post has been sponsored by zkPass team. At Shoal Research, we aim to ensure all content is objective and independent. Our internal review processes uphold the highest standards of integrity, and all potential conflicts of interest are disclosed and rigorously managed to maintain the credibility and impartiality of our research.